What do we make of the events in Europe? or in the USA? Are Donald Trump and Bernie Sanders inevitable products of an era dominated by a cultural evolution that is labeled post-modernism?
Nikil Saval at the New York Times titles his article on the new headquarters “campuses” being planned by Google and Apple as Google and Apple: the High-Tech Hippies of Silicon Valley. Back to the future?
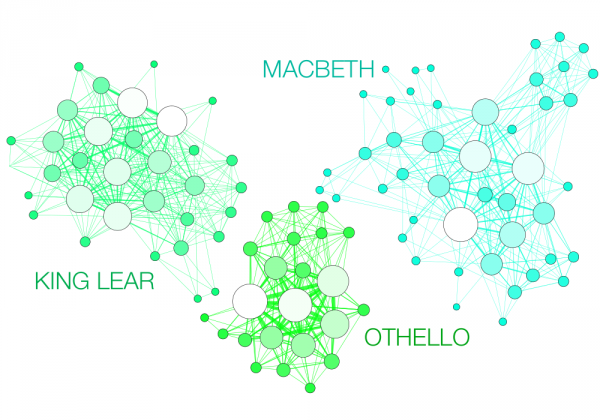
Every story has its architecture, its joints and crossbeams, ornaments and deep structure. The boundaries and scope of a story, its built environment, can determine the kind of story it is, tragedy, comedy, or otherwise. And every story also, it appears, generates a network—a web of weak and strong connections, hubs, and nodes.
Influencer marketing is all the rage right now, and according to a Tomoson study, it has become the fastest growing customer acquisition method online. A report from TapInfluence, a marketplace connecting brands with influencers, outlines the history and the impact of the rise of digital influencers.

At least everyone knows about encryption now. The post The Apple-FBI Battle Is Over, But the New Crypto Wars Have Just Begun appeared first on WIRED.

Today’s complicated data security landscape has begun to look a lot like a modern legend or fairytale. Just like King Arthur gathered his knights to fight against enemies and supernatural forces to find the Holy Grail, organizations are constantly fighting hackers, malicious individuals and human error, seeking the “Holy Grail” of data security – making themselves virtually “un-hackable.” In security, there’s a dangerous triad of motives formed by money, power and pride. This is because information is today’s currency and the power one can get with the right information is priceless. According to Security Intelligence, the average total cost of…

Donald Trump is the Gamergater of U.S. politics. He and his social media team uses Twitter in abusive ways that few might have predicted a serious contender for President of the United States would employ. But no blow is too low for Trump, and no smear too sexist, racist, or hate-filled.

With Apple set to argue its case against the FBI on March 22, Apple attorney Ted Olsen warned that the case is about more than meeting government demands to help break into an iPhone, it’s about fending off government agencies that seek ‘limitless’ powers to ‘listen to [our] conversations.’ You can imagine every different law enforcement official telling Apple we want a new product to get into something. Even a state judge could order Apple to build something. There’s no stopping point. That would lead to a police state. With the FBI admitting the Apple ID of a suspect in the San Bernadino
Taking a step beyond 2-D glyphs, Codeology depicts GitHub user activity based on what they have contributed as 3-D objects made of ASCII characters.
For over two decades, the battle between privacy-minded technologists and the U.S. government has primarily been over encryption. In the 1990s, in what became known as the Crypto Wars, the U.S. tried to limit powerful encryption — calling it as dangerous to export as sophisticated munitions — and eventually lost.
It’s a legal motion for the ages.
The response Apple lawyers filed Thursday to a court order that the company write software to defeat its own security protocols is exhaustive, fiery, accessible, and full of memorable passages.
The lawyers were asking a federal magistrate judge to vacate what they called her “unprecedented and oppressive” order demanding that Apple design and build software to hack into an iPhone used by San Bernardino killer Syed Rizwan Farook.
Copyright Bots Aren’t Always Bad, But They Shouldn’t Be in Charge
In 2007, Google built Content ID, a technology that lets rightsholders submit large databases of video and audio fingerprints and have YouTube continually scan new uploads for potential matches to those fingerprints. Since then, a handful of other user-generated content platforms have implemented copyright bots of their own that scan uploads for potential matches.
 Over the past several years numerous studies have looked at the effects of piracy on the music industry.
Over the past several years numerous studies have looked at the effects of piracy on the music industry.
One very consistent result seems to be that pirates are not by definition cheapskates. On the contrary, they tend to spend more money on merchandise, theater visits and concerts.
On Thursday, Apple filed its motion to vacate last week’s controversial judicial order requiring it to undermine device security for its iOS operating system. The company’s filing explains in compelling and forceful terms not only how thegovernment demands to which it responds would undermine national security and place millions of people at risk, but also why the FBI has chosen an inappropriate process through which to seek a groundbreaking new power that Congress has sensibly never granted.
Earlier this week, Facebook launched Reactions globally — allowing users to select which emotion a post evokes: like, love, haha, wow, sad or angry.
What’s missing in that list? Dislike.
Discover more from Erkan's Field Diary
Subscribe to get the latest posts sent to your email.
